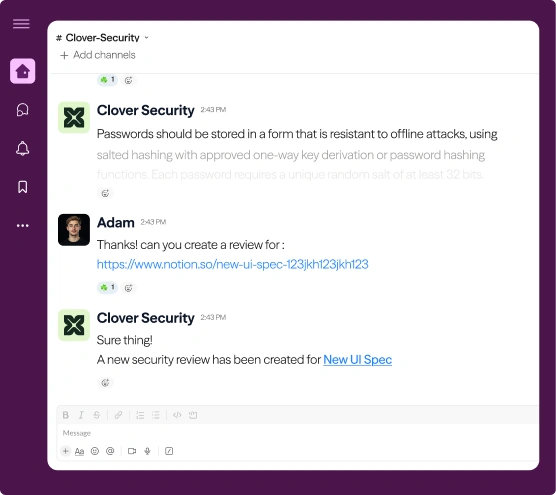
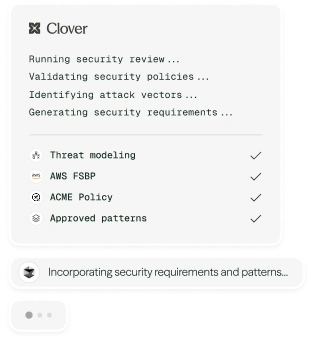
With Clover
How it works
Ingest & contextualize your standards
Pull in your organization’s standards, policies, and the industry frameworks you follow, then enrich them with product and threat context.
Codify reusable, approved patterns
Translate standards into clear, vetted patterns that builders can follow consistently without reinventing the wheel for common tasks.
Detect anti‑patterns & route remediation
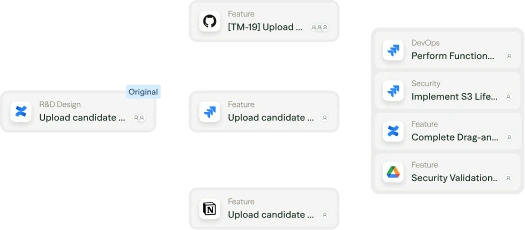
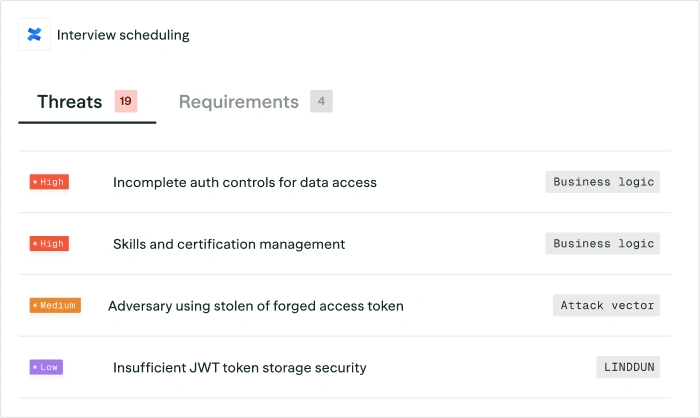
Continuously detect anti-patterns in code and design, surface them to security with context, and propose paved roads where approved patterns are missing.
Adapt standards to product and threat changes
Continuously update standards and policies using industry intel, product changes, incidents, and usage signals, and measure adoption, drift, and impact.
Integrates in minutes
Connect seamlessly to the tools you already use to extract context, route insights to builders, and make secure-by-design a natural part of your development flow.
Key benefits
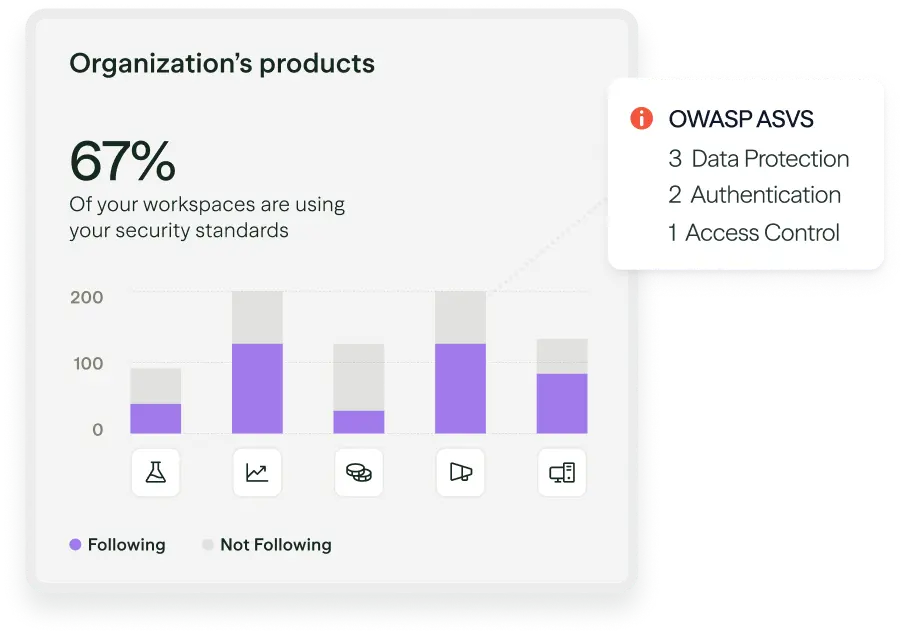
Actively mitigate risk
Continuously update standards to match how teams build and deliver secure, reusable patterns where work happens
Improvement
Lower risk by keeping standards current and eliminating outdated guidance.
Strengthen consistency
Give every team clear, reusable patterns so guidance and checks stay consistent across products and workflows.
Coverage
Increase alignment as more teams adopt the same vetted patterns.
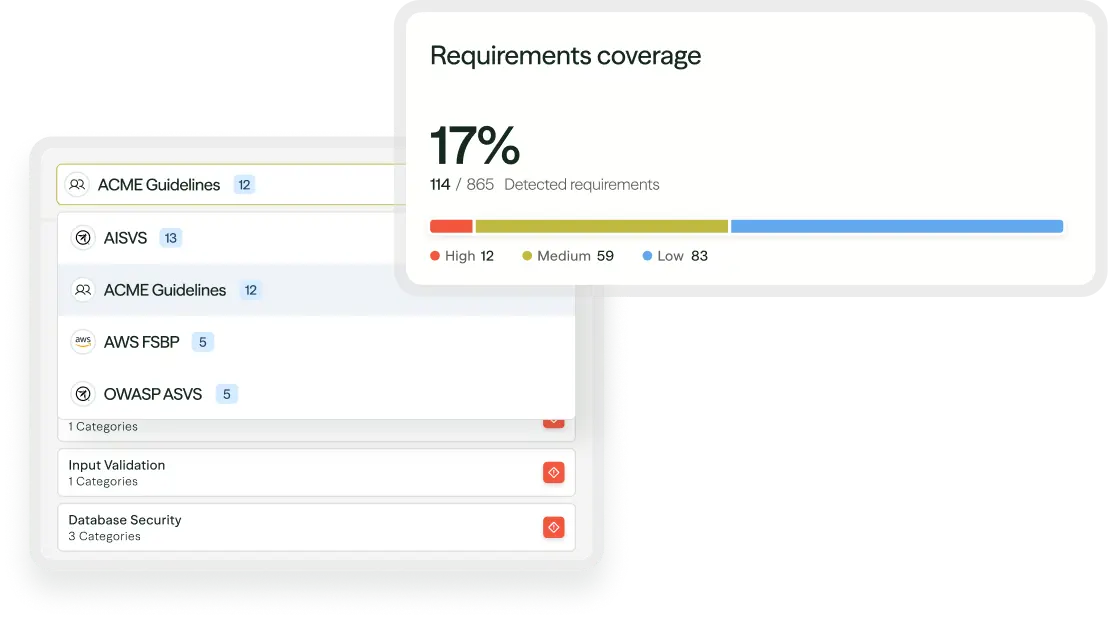
Raise your compliance bar
Blend industry frameworks with org-specific policies and map them to daily workflows for practical, auditable execution.
Adherence
Improve adherence by tying standards directly to real implementation.