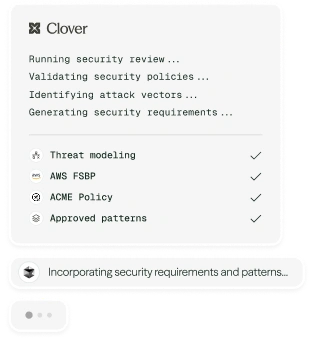
With Clover
How it works
Set your policy for risky changes
From authentication-related changes to sensitive data flows: define what changes should be surfaced through application-specific policies.
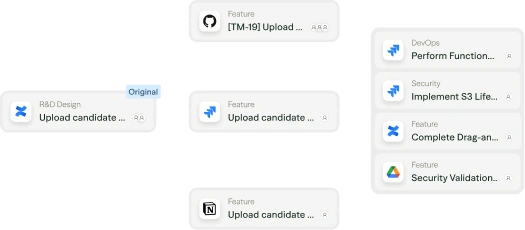
Collect context continuously
Gather design docs, tickets, architecture diagrams, code, pentest reports, and threat intel to maintain a live view of product, business, and security posture.
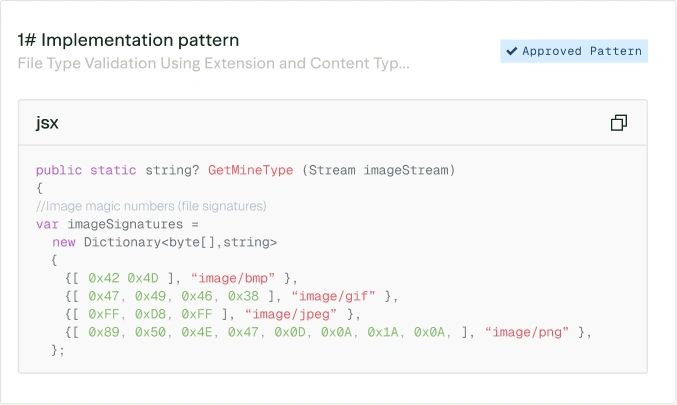
Assess and prioritize risks
Map features and changes to relevant controls and threats. Score each one by likelihood, impact, and posture to set priorities.
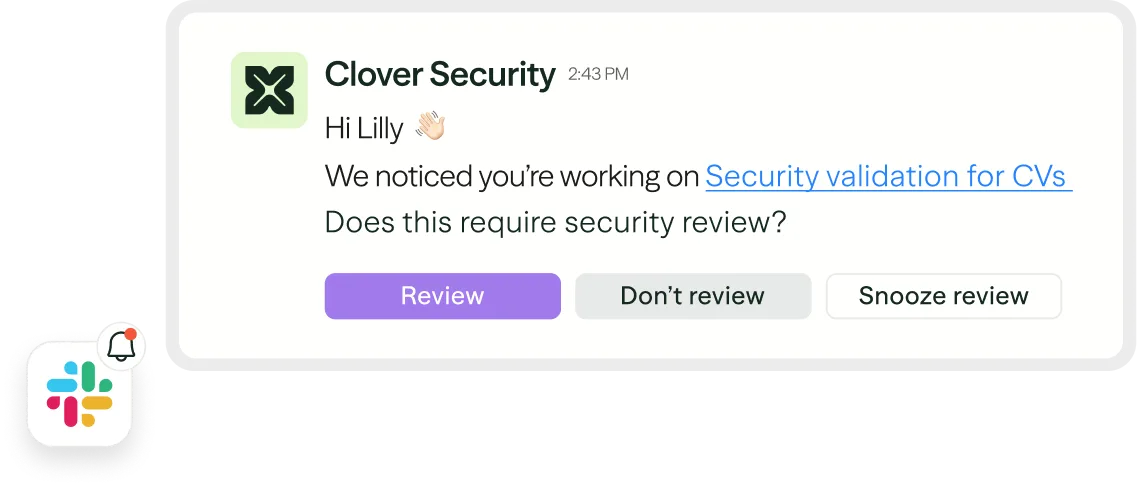
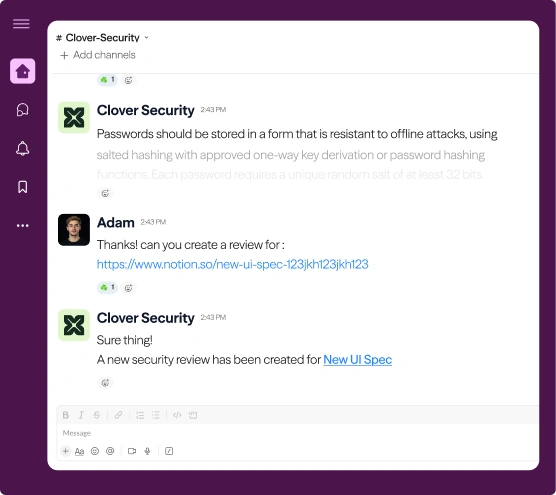
Notify and route actions
Automatically route risks to the right people at the right time, with the rationale, next steps, and workflow triggers needed for fast resolution.
Integrates in minutes
Connect seamlessly to the tools you already use to extract context, route insights to builders, and make secure-by-design a natural part of your development flow.
Key benefits
Reduce design risk early
Catch risk in design, before you write a single line of code.
Prevention
Identify and address design flaws before they turn into costly rework or late-stage fixes.
Improve control and focus
Ship faster and more simply with paved roads and fewer handoffs.
Precision
Direct effort with greater accuracy through automated risk scoring and prioritization.
Gain measurable confidence
Measure your coverage, adherence, and remediation metrics.
Insight
Quantify progress over time with live metrics on coverage and resolution.